

Stablecoins are transforming how businesses manage payments, offering faster transactions, global reach, and programmable features. But they come with risks that can lead to irreversible losses, especially in treasury management. Key risks include:
Misconfigured approvals: Errors in permissions can lead to accidental or fraudulent transfers.
Address substitution attacks: Fraudsters manipulate transaction histories to trick users into sending funds to fake wallets.
Insider errors or fraud: Mistakes or deliberate actions by employees can drain funds.
Sanctions compliance: Engaging with flagged entities or tainted funds can result in penalties or frozen operations.
Liquidity and de-peg risks: Stablecoins losing their $1 peg or market liquidity can disrupt cash flow.
Key Solutions:
MPC and multi-signature wallets: Require multiple approvals for transactions to prevent single points of failure.
Address allowlisting: Only send funds to pre-approved wallets.
Automated compliance checks: Screen transactions for sanctions and tainted funds.
Tiered wallets: Use separate wallets for small, routine payments and large reserves.
Liquidity planning: Diversify holdings and set limits to reduce exposure to market shocks.
Stablecoin treasuries can be safer by combining these strategies with automated tools and strict governance. The goal is to secure funds while maintaining efficiency.
The Role of Stablecoins, Risk Management Strategies, and Evolving Market Structure
Misconfigured Approvals and Unauthorized Transfers
In stablecoin treasury management, misconfigured approvals represent one of the most serious risks. These occur when permission settings or approval workflows allow unauthorized or accidental transfers. Since blockchain transactions are final and irreversible, a single error in configuration can lead to permanent and substantial losses.
How Misconfigured Approvals Occur
Misconfigured approvals often arise due to single points of failure - situations where a single individual or key has unchecked control over funds. If one person can request, approve, and sign a transaction without oversight, it opens the door to both insider fraud and accidental mistakes.
Relying on informal, manual processes like Slack messages or shared spreadsheets further increases the risk. These methods lack automated checks and proper segregation of duties, making errors or fraud more likely.
Another frequent issue is poor change management. For example, if changes to signer rosters, wallet allowlists, or spending limits are undocumented or unauthorized, malicious actors can exploit these gaps. Imagine a scenario where a former employee's signing authority isn't revoked after they leave the company - they could retain access to treasury wallets indefinitely.
Shared devices and credentials make matters worse. Using shared hardware for signing transactions or failing to remove unnecessary software from signing devices increases the risk of credential theft. Additionally, manually managing stablecoin minting and burning across multiple blockchains without automated controls raises the chances of configuration errors.
These risks highlight the importance of implementing strong, layered security measures to protect treasury operations.
How to Mitigate Approval Risks
The key to secure approvals is multi-person control. Use multi-signature (multisig) or Multi-Party Computation (MPC) wallets that require a quorum - such as 2-of-3 or 3-of-5 approvals - for any treasury movement. This eliminates single points of failure and ensures no one individual can transfer funds unilaterally.
"Separate the person who requests a payment from the person who approves and the person who signs." - BitGo
Segregation of duties is essential at every stage. The person initiating a payment should not be the same individual who approves it, and neither should act as the sole signer. This "dual control" system ensures independent oversight throughout the process.
Policy-as-code governance can further tighten security. By programmatically defining permissible assets, venues, and counterparty addresses, you can prevent unapproved transfers before they happen. Tools like Stablerail's Policy Console allow finance teams to enforce spending limits based on wallet tier, role, asset type, and counterparty, ensuring consistent governance.
Address allowlisting (whitelisting) is another critical safeguard. Maintain a board-approved list of destination addresses and venues to ensure funds cannot be sent to unauthorized wallets - even if a signer's credentials are compromised.
Wallet tiering adds an extra layer of security. Use "hot" wallets with strict velocity limits for small, automated transactions, while reserving "cold" vaults with offline signing and multi-person ceremonies for high-value reserves and large settlements. This approach ensures that significant transactions are subject to heightened scrutiny and cannot proceed without multiple approvals.
Finally, maintain tamper-proof logs of all approvals and signing events. Immutable audit trails are invaluable for compliance reviews and incident response, providing a clear record of who authorized each transaction and when.
Here’s a breakdown of key control types and how they enhance treasury security:
Control Type | Function | Treasury Benefit |
|---|---|---|
Multi-Person Approval | Requires multiple sign-offs for transfers above set thresholds. | Reduces risk of single points of failure or insider fraud. |
Address Whitelisting | Restricts transfers to pre-approved recipient addresses. | Prevents address substitution and accidental misrouting. |
Velocity Limits | Caps the value or number of transactions within a timeframe. | Limits potential losses from compromised accounts. |
Automated Screening | Conducts real-time checks against sanctions and AML blacklists. | Ensures compliance before funds are transferred. |
Time-Locks | Delays transaction execution for a set period after approval. | Provides a window to cancel unauthorized or erroneous transfers. |
Address Substitution Attacks and Social Engineering
Address substitution attacks, often referred to as "address poisoning", pose a serious risk to corporate stablecoin treasuries. Unlike traditional phishing, which typically focuses on stealing private keys, these attacks manipulate transaction histories to deceive users into sending funds to fraudulent wallets. Since blockchain transactions can't be reversed, even a small copy-paste mistake can lead to irreversible financial losses.
How Address Substitution Attacks Work
Attackers monitor blockchain activity to identify frequently used recipient addresses. They then create lookalike addresses that mimic key parts of trusted ones. To execute the attack, they send a small "dusting transaction" from the fake address, embedding it into your transaction history. This entry sits alongside legitimate transfers, increasing the chances that you'll mistakenly copy the attacker’s address for your next transaction.
In a major 2024 campaign, researchers uncovered 82,031 fake addresses - representing nearly 1% of all new Ethereum addresses - with a success rate of 0.03%. Despite the low success rate, the campaign generated $3 million in profits - 3,727 times the median scam profit - with victim wallets averaging $338,900 in losses across nearly 600 transfers.
The technical nature of these attacks is compounded by human error. Social engineering tactics exploit informal workflows, particularly in organizations with single points of failure where one compromised individual can both initiate and approve a transfer.
How to Prevent Address Substitution Attacks
Defending against these attacks requires multiple layers of security:
Use a trusted recipient allowlist: Maintain a board-approved list of verified wallet addresses. This ensures that funds are sent only to pre-approved destinations, even if credentials are compromised or transaction histories are manipulated.
Implement pre-signature checks: Tools like Stablerail's Treasury Hub can assess the risk of a counterparty address before a transaction is signed. These tools flag newly created addresses or those with no prior interaction with your treasury.
Verify full cryptographic addresses: Always confirm the entire cryptographic string of an address using a secure, external record. Interfaces that truncate addresses increase the risk of errors.
Enforce dual control: Separate the roles of initiating and approving transactions. This ensures independent verification of recipient addresses before funds are transferred.
Conduct small test transactions: Before transferring large sums, send a small test payment and confirm its receipt through an independent channel. This step can help identify inconsistencies and prevent costly errors.
Insider Errors and Fraud
Insider vulnerabilities rank high among risks to treasury operations, following approval misconfigurations and external threats. Even the most advanced security systems can’t shield against losses caused by human mistakes or intentional misconduct. Since blockchain transactions are irreversible, one wrong address or incorrect amount can lead to permanent loss of funds.
Common Insider Errors and Fraud Scenarios
Beyond system misconfigurations, insider errors and fraudulent activities can destabilize treasury operations. These risks typically fall into three main categories: accidental mistakes, unauthorized access, and deliberate fraud. For instance, a simple fat-finger error - like entering the wrong amount or pasting an incorrect recipient address - can drain funds from a corporate treasury in seconds. The manual handling of liquidity rebalancing further increases the likelihood of such errors.
Access control flaws introduce even greater risks. If a single employee has the authority to both request and approve transfers, they could exploit this power to redirect funds into personal accounts. In some cases, insiders may abuse their access to mint unauthorized tokens, alter system parameters, or activate emergency functions. As Elliptic highlights:
"Access control flaws allow unauthorized users to mint tokens, change parameters, or trigger emergency functions, posing major risks to stablecoin stability".
Torsion.ai underscores the severity of insider risks:
"One compromised laptop = complete loss of funds. Zero reversibility."
Additionally, liquidity traps can disrupt essential operations like payroll or supplier payments, amplifying operational risks. Insider fraud affecting reserve management can even turn treasury assets into liabilities.
How to Reduce Insider Risks
To mitigate insider risks, start by implementing segregation of duties. This ensures no single individual has unilateral control over funds. Pair this with multi-signature or MPC (multi-party computation) architectures, which require multiple authorized parties to approve a transaction before it’s executed.
Whitelisting withdrawals to pre-approved addresses is another critical safeguard, preventing funds from being sent to unauthorized destinations. Velocity limits and threshold policies add an extra layer of protection. For example, a payment exceeding $5,000 to a new address might require CFO approval, while weekend transfers over $10,000 could trigger additional verification steps.
Time locks offer an additional safety measure by introducing delays for high-risk operations. This delay provides stakeholders with a chance to identify and block unauthorized actions before they are executed on-chain. Every approval and signing event should also be recorded in immutable audit logs, tied to verified identities. This not only ensures accountability but also enables the detection of unusual behavior.
Tools like Stablerail's Treasury Hub streamline these processes by automating controls and providing plain-English risk reports. These reports flag suspicious activity - such as sudden large transfers or deviations from normal patterns - before transactions are signed. Its copilot verification system acts as a human-in-the-loop checkpoint, requiring approvers to review evidence and document any overrides. By shifting from informal procedures to structured, policy-driven approvals, treasury operations become significantly more secure.
Sanctions Compliance and Tainted Fund Risks
Treasury systems need to do more than just manage transactions and mitigate insider risks - they must also navigate the complex world of regulatory compliance. One of the less obvious but equally serious challenges for stablecoin treasuries is the risk of interacting with sanctioned entities or tainted funds. Even a single transaction with a flagged address can lead to enforcement actions, frozen operations, and significant reputational damage. While these risks may not be as visible as operational errors, they are just as critical.
What Are Sanctions and Taint Risks?
Sanctions risks emerge when a treasury engages with entities or addresses flagged by regulatory bodies like the U.S. Office of Foreign Assets Control (OFAC). Such interactions can result in hefty penalties, criminal or civil charges, and even secondary sanctions that could sever your organization's access to the U.S. financial system entirely. Regulatory interventions can freeze funds mid-transfer, disrupt essential payments like payroll, and lead to weeks or months of operational downtime due to investigations.
OFAC's rules are strict. For instance, any entity that is 50% or more owned by a sanctioned party is automatically considered blocked. This means treasuries must carefully map out complex networks of subsidiaries and ownership structures. A high-profile example occurred in October 2025, when OFAC designated Colombia's president, Gustavo Francisco Petro Urrego, under counternarcotics authorities. This move instantly created compliance risks for U.S. entities engaging with him.
Taint risks, on the other hand, involve funds that have been linked to mixers, sanctioned wallets, or other flagged sources. Even if your counterparty seems legitimate, blockchain analytics can trace the origin of funds back to illicit activities. Failure to comply with Know Your Customer (KYC) and Anti-Money Laundering (AML) standards often leads to severe fines and reputational fallout. OFAC has also signaled increased scrutiny of gatekeepers - such as investment advisors, accountants, and attorneys - who fail to address sanctions risks in their services. These challenges highlight the importance of automating compliance as part of a treasury's broader control framework.
How to Maintain Sanctions Compliance
Preventing regulatory missteps requires a proactive approach, starting with mandatory pre-signature screening at two critical points: during counterparty onboarding (via KYC/KYB processes) and immediately before executing payments. Automated sanctions screening tools should cross-check counterparty addresses against OFAC and other international blacklists to ensure no payments are authorized without a thorough review.
Geofencing controls can add another layer of protection by automatically blocking transactions from restricted jurisdictions or sanctioned regions. Additionally, performing taint analysis on funds ensures they haven’t passed through flagged entities. Maintaining an up-to-date list of approved and verified addresses - and regularly reviewing it - helps ensure transactions are limited to vetted parties. These checks should be enforced at every step of the payment process.
Platforms like Stablerail's Treasury Hub simplify compliance by automating these critical checks within their workflows. Before any payment is approved, agents conduct sanctions screening, taint analysis, and counterparty risk assessments. The system generates clear, actionable risk reports, flagging any potential exposures before execution. A final verification step requires approvers to review the evidence and document any necessary overrides. By shifting compliance from a manual process to an automated, policy-driven system, treasuries can better protect themselves from regulatory penalties and safeguard their reputation.
Liquidity and De-Peg Risks
Stablecoin treasuries face challenges not just from internal and compliance issues but also from unpredictable market dynamics. Even with stringent treasury controls in place, market events can destabilize stablecoins, leading to significant risks. While operational safeguards can defend against errors and attacks, they can't shield against broader market disruptions that cause stablecoins to lose their dollar peg or become hard to redeem. In such scenarios, liquidity crises can freeze operations, trap funds, and force treasuries to sell assets at a loss just to access cash.
What Are Liquidity and De-Peg Risks?
A stablecoin "de-peg" occurs when its value drops below $1.00 due to intense selling pressure. The underlying issue here is liquidity - stablecoins rely on deep market reserves to handle trading demands, but that liquidity can vanish during times of stress.
Take, for example, the case of Circle's USDC in March 2023. Its value plunged to $0.87 after news broke that $3.3 billion (around 8% of its reserves) was tied up in the collapsed Silicon Valley Bank. Redemptions were halted until government action restored confidence and brought the peg back to $1. A similar event unfolded on October 10, 2025, when Ethena Labs' algorithmic stablecoin, USDe, sank to $0.65 on Binance. A massive selloff, fueled by rising U.S.–China trade tensions, triggered the drop. Technical glitches on exchanges delayed the arbitrage process, prolonging the crisis.
"The possibility of depegging is not just hypothetical. Indeed, we have already experienced large depegging events - one as recently as last month."
Marco Macchiavelli, BPI
The type of stablecoin plays a major role in how these risks unfold. Fiat-backed stablecoins like USDC and USDT depend on the creditworthiness and liquidity of their reserves, which often include cash, U.S. Treasuries, and commercial paper. On the other hand, algorithmic stablecoins rely entirely on market trust, making them vulnerable to "death spirals", where falling prices lead to panic selling. Risks also arise from reserve-related issues, such as bank failures or technical vulnerabilities like smart contract hacks.
In many cases, direct redemptions are only available to institutional investors, leaving smaller holders to depend on secondary markets. During a crisis, these markets can dry up quickly, making it difficult to trade stablecoins. Additionally, treasuries that lend stablecoins on decentralized finance (DeFi) platforms may find themselves stuck in "liquidity traps." This can happen if the platform's collateral sharply loses value or if the platform freezes asset prices to prevent liquidations.
Given these risks, treasuries must adopt stablecoin treasury management best practices to navigate potential market disruptions.
How to Manage Liquidity Risks
Managing liquidity and de-peg risks requires a proactive, market-oriented approach. While internal controls address operational vulnerabilities, these external risks demand strategies that combine exposure limits, real-time monitoring, and contingency planning.
Start by setting strict exposure limits and diversifying holdings across multiple stablecoin issuers. This reduces the impact of a single de-peg event. However, be cautious of correlation risks - during systemic crises, multiple stablecoins can lose their pegs simultaneously. Maintaining a mix of fiat reserves and stablecoins can provide liquidity in volatile markets. Partnering with multiple settlement providers or over-the-counter (OTC) desks can also help execute large trades without significant price slippage.
Due diligence is essential. Evaluate stablecoin issuers for asset quality, custody protocols, and redemption processes. Use real-time monitoring tools to track key metrics like peg stability, trading volumes, and market depth. These tools can offer early warnings of potential de-pegging events. Additionally, establish contingency plans with clear "trigger points." For example, decide in advance to reduce exposure if a stablecoin trades below $0.98 for more than 30 minutes. It's also crucial to identify alternative liquidity sources before a crisis hits.
Platforms like Stablerail's Treasury Hub offer integrated solutions by embedding these safeguards directly into payment workflows. By combining automated controls with strong governance, treasuries can protect themselves from market-wide risks while maintaining operational agility. No internal measure can fully eliminate these risks, but thoughtful planning can minimize their impact.
Building a Secure Stablecoin Treasury Framework
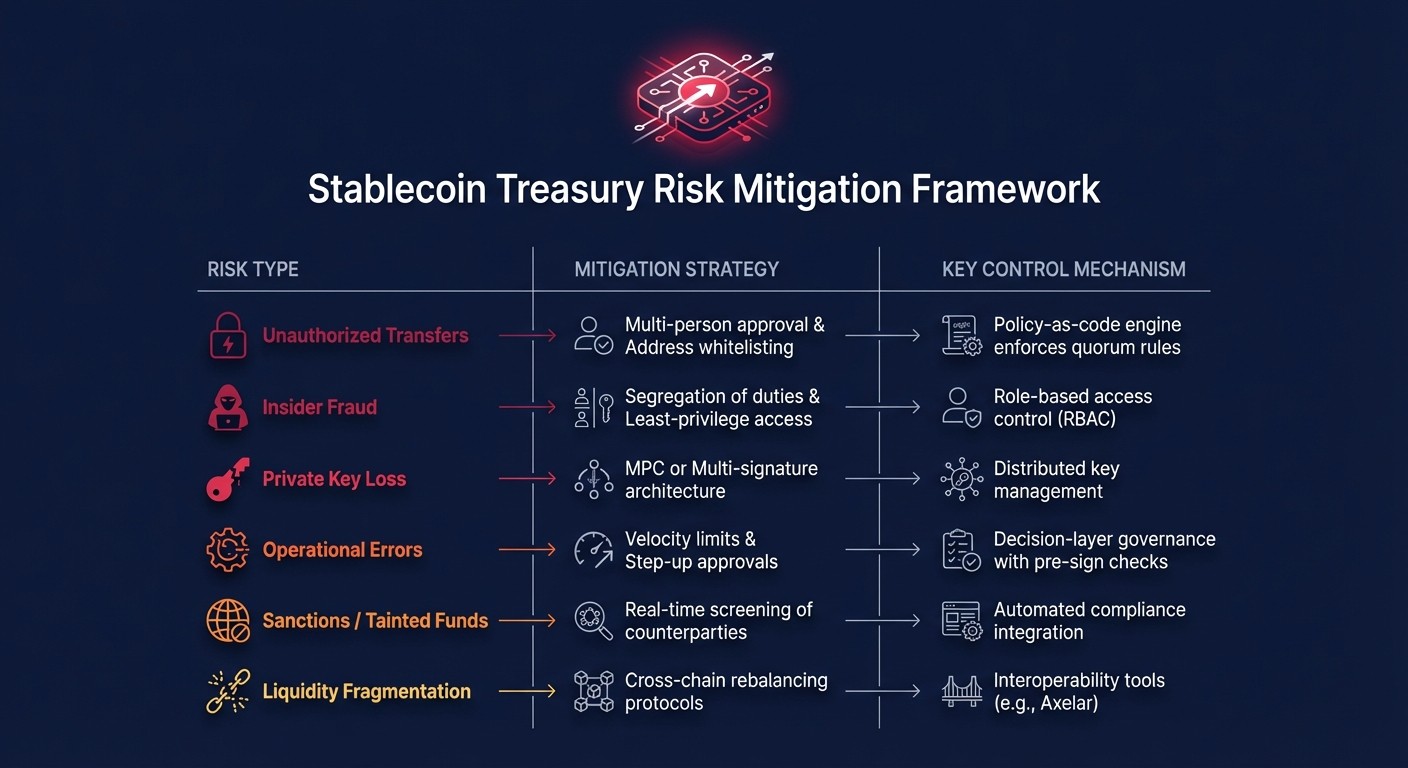
Stablecoin Treasury Risk Mitigation Strategies and Control Mechanisms
Managing risks such as unauthorized transfers or liquidity shocks demands a well-thought-out framework. This framework should automate governance, distribute key responsibilities to eliminate single points of failure, and maintain detailed logs of every action. The aim is to create a control environment that aligns with corporate treasury standards while retaining the efficiency and flexibility of on-chain operations. Below, we’ll explore the core components needed to build such a secure and efficient system.
Core Components of a Secure Framework
A robust stablecoin treasury starts with self-custodial MPC (Multi-Party Computation) wallets. Unlike traditional multi-signature setups that enforce policies directly on-chain, MPC splits the private key material across multiple participants. This ensures no single individual or device holds the entire key, reducing the risk of a compromised device draining funds. For organizations managing large reserves, implementing a tiered wallet structure is essential:
Cold vaults for long-term holdings.
Warm wallets for routine settlements, requiring quorum approvals.
Hot wallets for low-value, automated transactions, equipped with strict velocity limits.
The next critical element is a policy-as-code engine that converts board-approved guidelines into enforceable machine rules. Instead of relying on manual reviews, this system automatically verifies every transaction against preset parameters like spending limits, asset types, counterparties, and time windows. These checks occur before any transaction is signed, reducing the risk of irreversible mistakes reaching the blockchain.
"Separate the person who requests a payment from the person who approves and the person who signs." - BitGo
Segregation of duties is another cornerstone of this framework. By ensuring that the initiator, approver, and signer are distinct individuals, organizations can minimize insider risks. Coupled with least-privilege access - where users are granted only the permissions necessary for their roles - and immutable audit trails for every signing event, this setup helps meet SOC 1/SOC 2 audit requirements.
Compliance should be embedded into every payment workflow. Automated checks, such as real-time sanctions screening against OFAC lists, crypto compliance verifications, and adherence to the Travel Rule, should complement pre-signature controls. These measures ensure that problematic funds are flagged before entering the treasury and that international payments meet regulatory standards without manual intervention. For operations spanning multiple blockchains, interoperability tools like Axelar facilitate liquidity management through burn-and-mint protocols, allowing treasuries to handle reserves efficiently from a single interface.
Risk Mitigation Comparison Table
Here’s a breakdown of the main risks, along with their mitigation strategies and control mechanisms:
Risk Type | Mitigation Strategy | Key Control Mechanism |
|---|---|---|
Unauthorized Transfers | Multi-person approval & Address whitelisting | Policy-as-code engine enforces quorum rules |
Insider Fraud | Segregation of duties & Least-privilege access | Role-based access control (RBAC) |
Private Key Loss | MPC or Multi-signature architecture | Distributed key management |
Operational Errors | Velocity limits & Step-up approvals | Decision-layer governance with pre-sign checks |
Sanctions / Tainted Funds | Real-time screening of counterparties | Automated compliance integration |
Liquidity Fragmentation | Cross-chain rebalancing protocols | Interoperability tools (e.g., Axelar) |
Solutions like Stablerail's Treasury Hub integrate these components into a unified control system. Positioned above custody and before signing, this platform enforces governance at the decision-making stage. By combining MPC-secured vaults, policy-as-code engines, and pre-signature risk checks, treasuries can achieve the speed and efficiency of blockchain settlements without compromising on the control and oversight expected in traditional finance. This proactive approach not only manages risks but also prevents them from arising in the first place.
Conclusion
Managing a stablecoin treasury comes with its own set of challenges that are quite different from those faced in traditional banking. These include risks like misconfigured approvals, address substitution attacks, insider fraud, sanctions exposure, and liquidity shocks. What sets secure operations apart from disastrous losses is whether the right controls are in place before a transaction hits the blockchain. Once a blockchain transaction goes through, there’s no taking it back.
Pre-signature controls are critical for addressing these risks. Tools such as MPC-secured wallets, policy-as-code engines, and segregation of duties help prevent unauthorized transfers and operational blunders at the decision-making stage. Real-time sanctions screening and automated compliance checks ensure that problematic funds are identified and blocked before they enter the treasury. Additionally, tiered wallet structures and velocity limits act as safeguards to minimize potential damage. These strategies become even more crucial as the stablecoin market grows and regulations continue to shift.
The numbers show it: the stablecoin market is expanding rapidly, and with it comes the need for stronger treasury controls. As institutional adoption rises and compliance requirements grow stricter, manual processes simply can’t keep up with today’s fast-moving environment.
Industry leaders recognize this shift:
"The companies that build around these new possibilities will determine what finance becomes." - Valla Vakili
Ultimately, securing a stablecoin treasury isn’t about eliminating risk entirely - it’s about managing it effectively. The key is making risks visible, measurable, and manageable through enforceable policies and constant monitoring. The strategies outlined here offer a way to balance the speed and efficiency of blockchain settlements with the control and oversight that corporate finance demands.
FAQs
How can businesses protect stablecoin transactions from address substitution attacks?
To protect stablecoin transactions from address substitution attacks, businesses should incorporate multiple layers of security into their workflows. Start with a pre-signature governance process - this step verifies destination addresses against an approved whitelist before any signing keys are released. By doing so, you ensure that only authorized addresses are used, blocking any unauthorized changes.
Next, integrate multi-signature approval into your process. This requires two or more independent parties to confirm the destination address, adding an extra checkpoint to catch errors or malicious actions before they escalate.
In addition, make use of real-time monitoring and alert systems to track transaction activity. These tools can quickly flag unusual patterns or sudden address changes, giving treasury teams the chance to pause payments before they’re finalized, which helps prevent irreversible mistakes. Lastly, enforce clear policies such as regular address audits, “sign-off-before-send” procedures, and frequent testing in a secure environment. When combined, these practices create a solid defense against address substitution attacks.
What are the best strategies to manage liquidity and prevent de-pegging risks in stablecoin treasuries?
To address liquidity risk, it's crucial to maintain a reserve of high-quality, short-term assets. Examples include U.S. Treasury securities, AA-rated commercial paper, repo agreements, and insured bank deposits. These assets can be quickly converted to cash, allowing for smooth handling of sudden redemption surges without resorting to distressed sales. Diversifying across different liquid assets minimizes concentration risk, while regular stress tests ensure the reserve is adequately sized to meet potential demands. Additionally, keeping transaction costs low when converting stablecoins to fiat can discourage panic-driven withdrawals and help maintain the peg.
For managing de-pegging risks, transparency plays a vital role. Frequent, independent audits of reserves and real-time disclosures about the backing assets build trust and reduce market speculation that could lead to de-pegging. A well-balanced reserve of liquid, high-quality assets reassures stakeholders, while governance policies requiring pre-approval for changes to reserve composition provide an added layer of security against unforeseen risks.
Why is separating duties critical for preventing insider fraud in stablecoin treasury management?
Separating duties is a key pillar of stablecoin treasury management because it ensures no single individual wields unchecked control over critical operations. By splitting responsibilities - like initiating, approving, and executing transactions - organizations can dramatically lower the risk of insider fraud. This setup ensures that no one person can move funds, change wallet permissions, or conceal fraudulent activities without oversight.
Another advantage of this system is the creation of clear audit trails. These trails make it easier to spot irregularities during reviews or reconciliations. If someone attempts to bypass established controls, mismatches between assigned roles can trigger alerts. Plus, requiring multiple approvals makes it harder for collusion to occur. In a space where even small errors can result in irreversible financial losses, dividing duties transforms individual control into shared accountability, safeguarding both assets and the organization’s reputation.
Related Blog Posts
Ready to modernize your treasury security?
Latest posts
Explore more product news and best practices for using Stablerail.


